Hacking back is all the rage. Sometimes the victims of cyberattacks will retaliate against their intruders and try to wipe stolen data, identify their attackers, or stop a campaign by deploying their own, often legally dubious, tools.
Now, a high-profile plastic-surgery practice in London that caters to a number of celebrity clients has seemingly fought back against hackers who stole a bevy of sensitive customer photos, and has tried to unmask the assailants. The news provides another example of hacking back, which rarely becomes public, while U.S. lawmakers are gaining more support for a plan to make such counterattacks legal.
“We’ve encountered a few petty, yet brazen, attempts to collect intelligence about us,” someone from the hacking group the Dark Overlord, which targeted the plastic surgeon, told The Daily Beast.
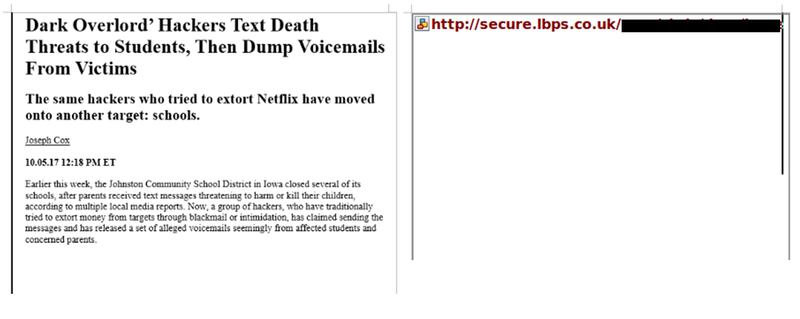
In October, The Daily Beast reported the hackers had targeted London Bridge Plastic Surgery (LBPS), which describes itself as “one of the leading plastic-surgery clinics in the U.K.” on its website. LBPS clients include TV star Katie Price and other celebrities. At the time, the Dark Overlord provided The Daily Beast with dozens of highly graphic and close-up images of surgery on male and female genitalia stolen from the practice.
But, it appears the doctors tried to gather information on the Dark Overlord with a small hack of their own.
The hackers shared a Word document with The Daily Beast that the group says Chris Inglefield, LBPS’ chief surgeon, sent to them. According to the metadata of the file, it was created Oct. 19, before the hack became public. The file includes snippets of two articles about the Dark Overlord, including one written by this reporter.
Ostensibly, this is an innocuous file, but, in reality, it contains no text at all. The two articles are actually part of an image stored on a server belonging to LBPS. When the target opens the document, it opens a connection and retrieves the image from LBPS’ server, meaning LBPS now has the target’s IP address. With this, authorities could subpoena a relevant internet service provider, and find out who is behind it—assuming, of course, the suspect is not using Tor or some other protection which masks a user’s original IP address.
Various law-enforcement agencies have used similar techniques to identify child pornographers, sextortionists, and those trying to illegally buy weapons online, but typically after obtaining a warrant. In some cases, such as this one, private companies or individuals may try it themselves, too, but the legality of such tactics can be murky.
The Daily Beast verified that the image of the articles is still hosted on LBPS’ server, and that when opened, the document retrieves this image from the server. The image, called “jonresearch.png” is stored inside a directory called “chris,” indicating it may belong to Inglefield.
Representatives for LBPS did not respond to multiple requests for comment Thursday.
“We confronted Christopher about his attempt to de-anonymize us, and he denied it vehemently. Although, we’ll point out that this attempt was located on his user share of his own company’s server. We punished Christopher accordingly,” the Dark Overlord told The Daily Beast.
The surgical practice’s attempt was not successful, according to The Dark Overlord.
“Any threat actor group worth their salt has built systems to safely interact with these attempts. While any attempt is concerning, it’s extremely unlikely the potential client is sitting on an abundance of unknown exploits,” they added.
In Washington on Monday, seven new co-sponsors joined support for the Active Cyber Defense Certainty Act (ACDC), which would legalize many hack-back techniques and give stronger legal footing to the sort of thing LBPS appears to have carried out. Under the ACDC, private companies will be able to leave their own network to establish who was behind an attack, disrupt attacks without damaging others’ computers, retrieve and destroy stolen files, monitor the behavior of an attacker, and use “beaconing” technology, according to a press release from Rep. Tom Graves (R-GA), who drafted the bill. Beaconing is essentially the technique in this LBPS example—somehow getting an attacker to trigger a trap that reveals their own location.
Although obviously talking about much more serious instances, in which companies may deploy fully fledged malware or hacking tools, former National Security Agency Director Gen. Keith Alexander told reporters this week that hacking back could start wars, Motherboard reported.
As for the plastic-surgery practice’s and others’ attempts, the Dark Overlord is not dismayed.
“In all cases, it amounts only to a fair bit of chuckling around the office,” they said.